Hipster
Hipster · 11 September 2023
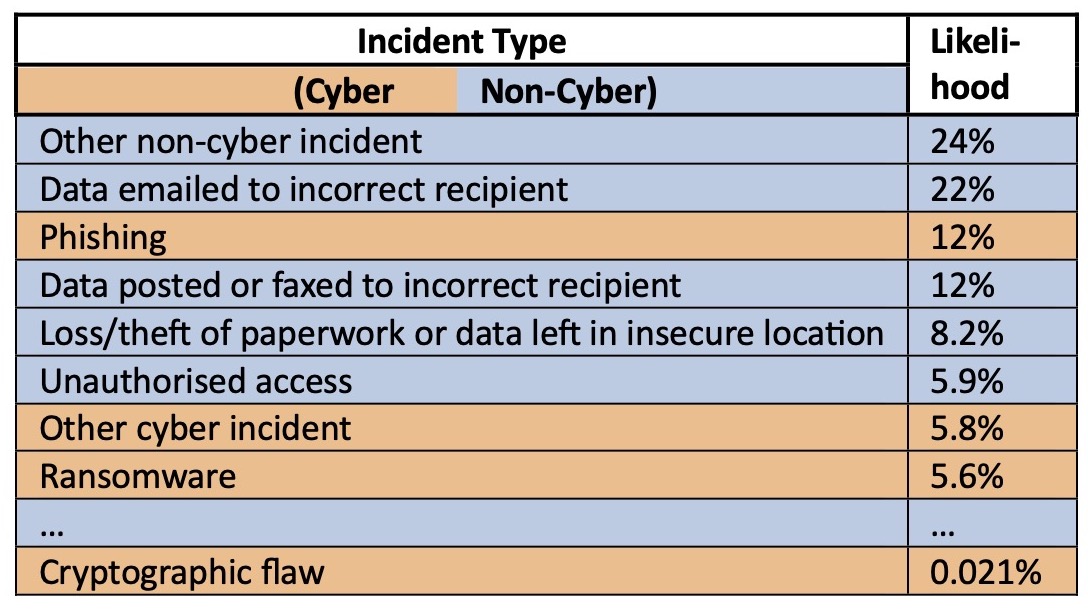
Security and privacy problems are not just hackers. Overlooked everyday risks can multiply fast!
Hipster · 02 February 2023
How the concept of Absorptive Capacity can help us get value out of cybersecurity in product innovation.
Hipster · 12 December 2022
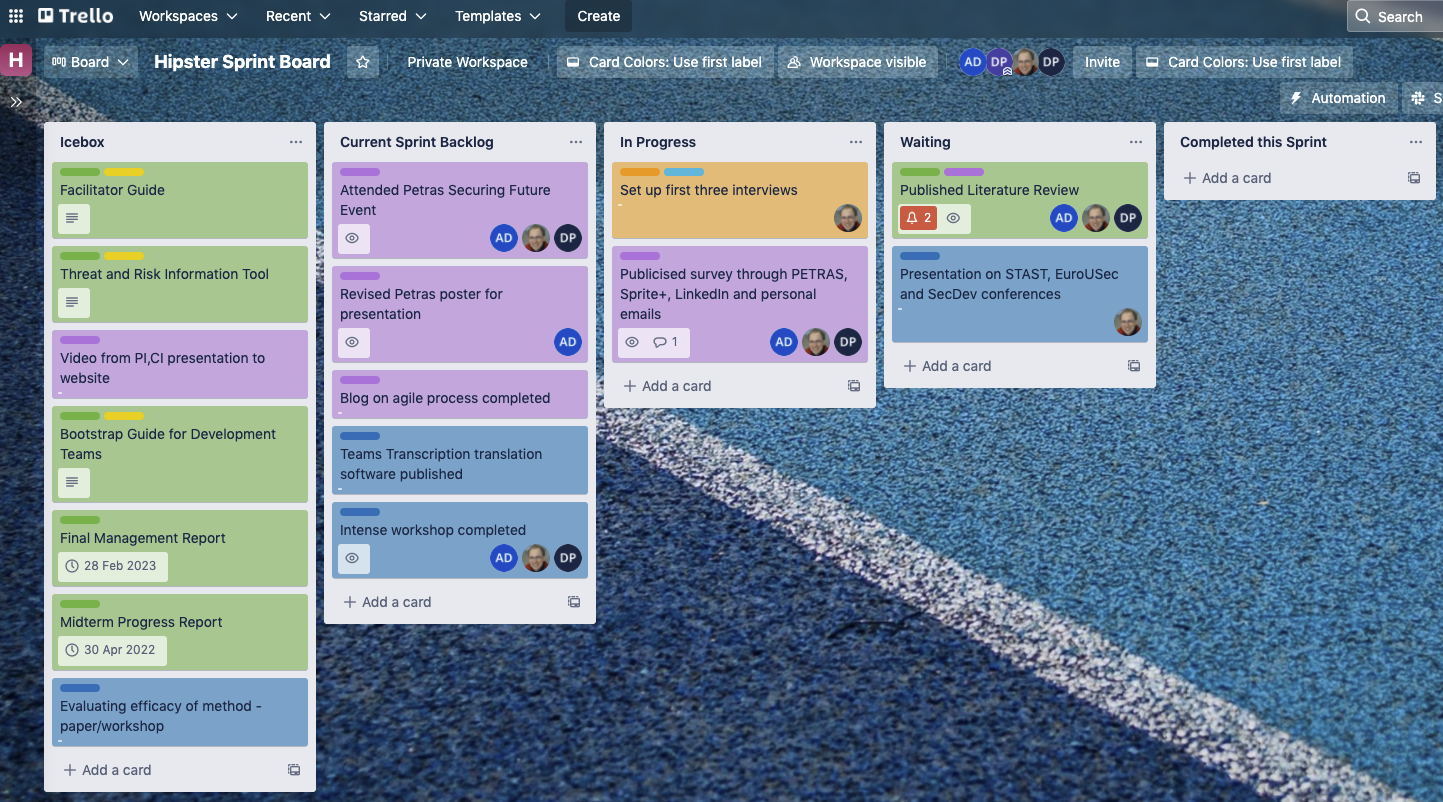
Agile research projects need a minimal project manager role to act as customer.
Hipster · 08 May 2022
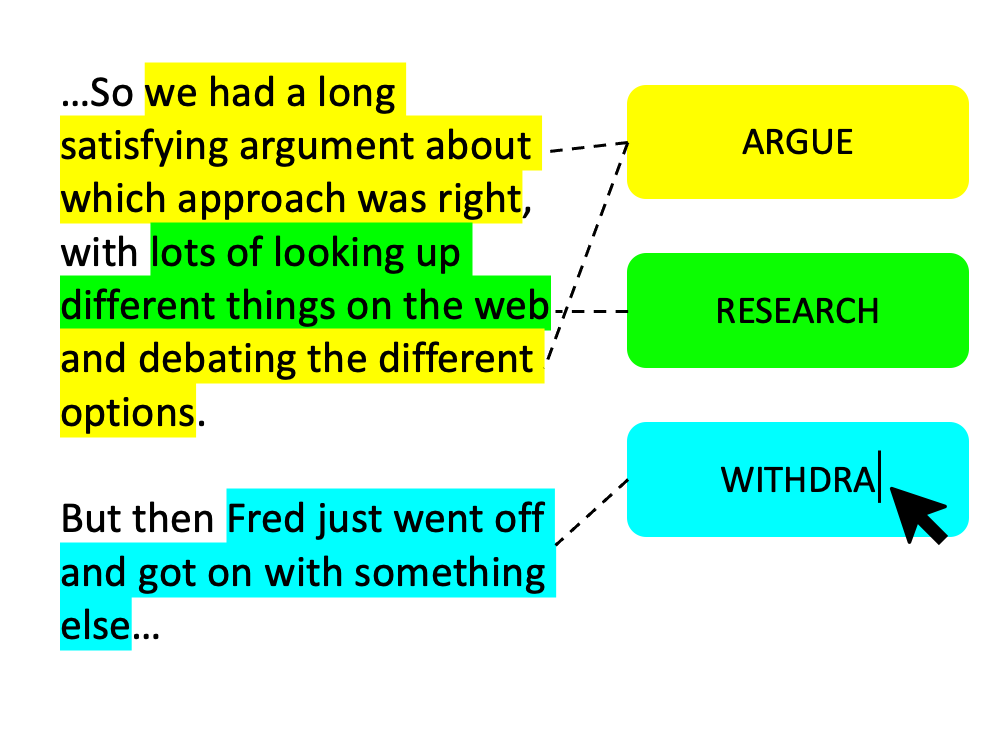
A key output of open coding is an huge number of open codes. How are you to make sense out of that seeming chaos?
Hipster · 20 March 2022
Is double open coding possible? Here in the Hipster project, we have found that not only is the answer ‘yes’, but also that the benefits are considerable. Read on to learn why.